Request Demo
What are ASA replacements and how do they work?
21 June 2024
Introduction to ASA replacements
In the rapidly evolving landscape of network security, Adaptive Security Appliances (ASAs) have long been the cornerstone for safeguarding organizational data. However, as technology advances and the demands on network infrastructure increase, the need for more robust and flexible solutions becomes evident. This is where ASA replacements come into play. Designed to provide enhanced security measures, greater scalability, and improved performance, these replacements are becoming essential for modern enterprises. This blog post will delve into how ASA replacements work and what they are used for, providing you with a comprehensive understanding of their importance in today's cybersecurity framework.
How do ASA replacements work?
ASA replacements integrate advanced security features and functionalities that surpass traditional ASAs. The primary objective is to offer a more holistic approach to network security, combining multiple security services into a unified solution. Here's how they achieve this:
1. **Next-Generation Firewall Capabilities**: Unlike traditional ASAs, which primarily focus on stateful inspection and packet filtering, ASA replacements come equipped with next-generation firewall (NGFW) capabilities. These include deep packet inspection, intrusion prevention systems (IPS), and application layer filtering. By analyzing traffic at a more granular level, NGFWs can detect and block sophisticated threats that older systems might miss.
2. **Unified Threat Management**: ASA replacements often feature Unified Threat Management (UTM), which consolidates various security functions such as antivirus, anti-malware, content filtering, and VPN (Virtual Private Network) services into a single device. This unified approach simplifies management and reduces the administrative overhead associated with maintaining multiple security appliances.
3. **Scalability and Flexibility**: Modern ASA replacements are designed to scale with an organization's growth. They support a wide range of deployment options, including on-premises, cloud-based, and hybrid environments. This flexibility ensures that businesses can adapt their security posture as their needs evolve, without the need for significant hardware investments.
4. **Automation and Threat Intelligence**: Leveraging advancements in artificial intelligence (AI) and machine learning (ML), ASA replacements can automate threat detection and response processes. They can integrate with threat intelligence platforms to receive real-time updates on emerging threats, enabling proactive defense mechanisms. This level of automation not only enhances security but also frees up IT resources to focus on strategic initiatives.
5. **Advanced VPN Capabilities**: With the rise of remote work, secure access to company resources is more critical than ever. ASA replacements support advanced VPN technologies, including Secure Sockets Layer (SSL) and Internet Protocol Security (IPsec) VPNs. These features ensure that remote connections are encrypted and secure, safeguarding sensitive data from potential breaches.
What are ASA replacements used for?
ASA replacements are utilized across various industries and sectors to address a multitude of security challenges. Here are some of the primary use cases:
1. **Enhanced Network Security**: At their core, ASA replacements provide robust network security by protecting against a wide array of threats, including malware, ransomware, phishing attacks, and unauthorized access. Their advanced features ensure comprehensive protection for both perimeter and internal networks.
2. **Regulatory Compliance**: Many industries are subject to stringent regulatory requirements regarding data protection and privacy. ASA replacements help organizations meet compliance standards such as GDPR, HIPAA, and PCI-DSS by providing detailed logging, reporting, and auditing capabilities. These features are crucial for demonstrating adherence to regulatory frameworks and avoiding costly penalties.
3. **Secure Remote Access**: With the increasing prevalence of remote work, securing remote access to corporate networks has become a top priority. ASA replacements offer robust VPN solutions that facilitate secure and seamless connectivity for remote employees. This ensures that sensitive information remains protected, regardless of where employees are located.
4. **Data Center Security**: ASA replacements play a vital role in securing data centers, which are often targets for cyber-attacks due to the valuable information they store. By implementing advanced security measures, organizations can safeguard their data centers against breaches and ensure the integrity and availability of critical services.
5. **Threat Detection and Response**: Modern cyber threats are highly sophisticated and can bypass traditional security measures. ASA replacements, with their advanced threat detection and response capabilities, enable organizations to identify and mitigate threats in real-time. This proactive approach minimizes the potential impact of cyber incidents and ensures a swift recovery.
In conclusion, ASA replacements are indispensable tools in the modern cybersecurity arsenal. By offering advanced features, scalability, and comprehensive protection, they address the limitations of traditional ASAs and provide a robust defense against the evolving threat landscape. Whether enhancing network security, ensuring regulatory compliance, or securing remote access, ASA replacements are crucial for safeguarding organizational data and maintaining business continuity.
In the rapidly evolving landscape of network security, Adaptive Security Appliances (ASAs) have long been the cornerstone for safeguarding organizational data. However, as technology advances and the demands on network infrastructure increase, the need for more robust and flexible solutions becomes evident. This is where ASA replacements come into play. Designed to provide enhanced security measures, greater scalability, and improved performance, these replacements are becoming essential for modern enterprises. This blog post will delve into how ASA replacements work and what they are used for, providing you with a comprehensive understanding of their importance in today's cybersecurity framework.
How do ASA replacements work?
ASA replacements integrate advanced security features and functionalities that surpass traditional ASAs. The primary objective is to offer a more holistic approach to network security, combining multiple security services into a unified solution. Here's how they achieve this:
1. **Next-Generation Firewall Capabilities**: Unlike traditional ASAs, which primarily focus on stateful inspection and packet filtering, ASA replacements come equipped with next-generation firewall (NGFW) capabilities. These include deep packet inspection, intrusion prevention systems (IPS), and application layer filtering. By analyzing traffic at a more granular level, NGFWs can detect and block sophisticated threats that older systems might miss.
2. **Unified Threat Management**: ASA replacements often feature Unified Threat Management (UTM), which consolidates various security functions such as antivirus, anti-malware, content filtering, and VPN (Virtual Private Network) services into a single device. This unified approach simplifies management and reduces the administrative overhead associated with maintaining multiple security appliances.
3. **Scalability and Flexibility**: Modern ASA replacements are designed to scale with an organization's growth. They support a wide range of deployment options, including on-premises, cloud-based, and hybrid environments. This flexibility ensures that businesses can adapt their security posture as their needs evolve, without the need for significant hardware investments.
4. **Automation and Threat Intelligence**: Leveraging advancements in artificial intelligence (AI) and machine learning (ML), ASA replacements can automate threat detection and response processes. They can integrate with threat intelligence platforms to receive real-time updates on emerging threats, enabling proactive defense mechanisms. This level of automation not only enhances security but also frees up IT resources to focus on strategic initiatives.
5. **Advanced VPN Capabilities**: With the rise of remote work, secure access to company resources is more critical than ever. ASA replacements support advanced VPN technologies, including Secure Sockets Layer (SSL) and Internet Protocol Security (IPsec) VPNs. These features ensure that remote connections are encrypted and secure, safeguarding sensitive data from potential breaches.
What are ASA replacements used for?
ASA replacements are utilized across various industries and sectors to address a multitude of security challenges. Here are some of the primary use cases:
1. **Enhanced Network Security**: At their core, ASA replacements provide robust network security by protecting against a wide array of threats, including malware, ransomware, phishing attacks, and unauthorized access. Their advanced features ensure comprehensive protection for both perimeter and internal networks.
2. **Regulatory Compliance**: Many industries are subject to stringent regulatory requirements regarding data protection and privacy. ASA replacements help organizations meet compliance standards such as GDPR, HIPAA, and PCI-DSS by providing detailed logging, reporting, and auditing capabilities. These features are crucial for demonstrating adherence to regulatory frameworks and avoiding costly penalties.
3. **Secure Remote Access**: With the increasing prevalence of remote work, securing remote access to corporate networks has become a top priority. ASA replacements offer robust VPN solutions that facilitate secure and seamless connectivity for remote employees. This ensures that sensitive information remains protected, regardless of where employees are located.
4. **Data Center Security**: ASA replacements play a vital role in securing data centers, which are often targets for cyber-attacks due to the valuable information they store. By implementing advanced security measures, organizations can safeguard their data centers against breaches and ensure the integrity and availability of critical services.
5. **Threat Detection and Response**: Modern cyber threats are highly sophisticated and can bypass traditional security measures. ASA replacements, with their advanced threat detection and response capabilities, enable organizations to identify and mitigate threats in real-time. This proactive approach minimizes the potential impact of cyber incidents and ensures a swift recovery.
In conclusion, ASA replacements are indispensable tools in the modern cybersecurity arsenal. By offering advanced features, scalability, and comprehensive protection, they address the limitations of traditional ASAs and provide a robust defense against the evolving threat landscape. Whether enhancing network security, ensuring regulatory compliance, or securing remote access, ASA replacements are crucial for safeguarding organizational data and maintaining business continuity.
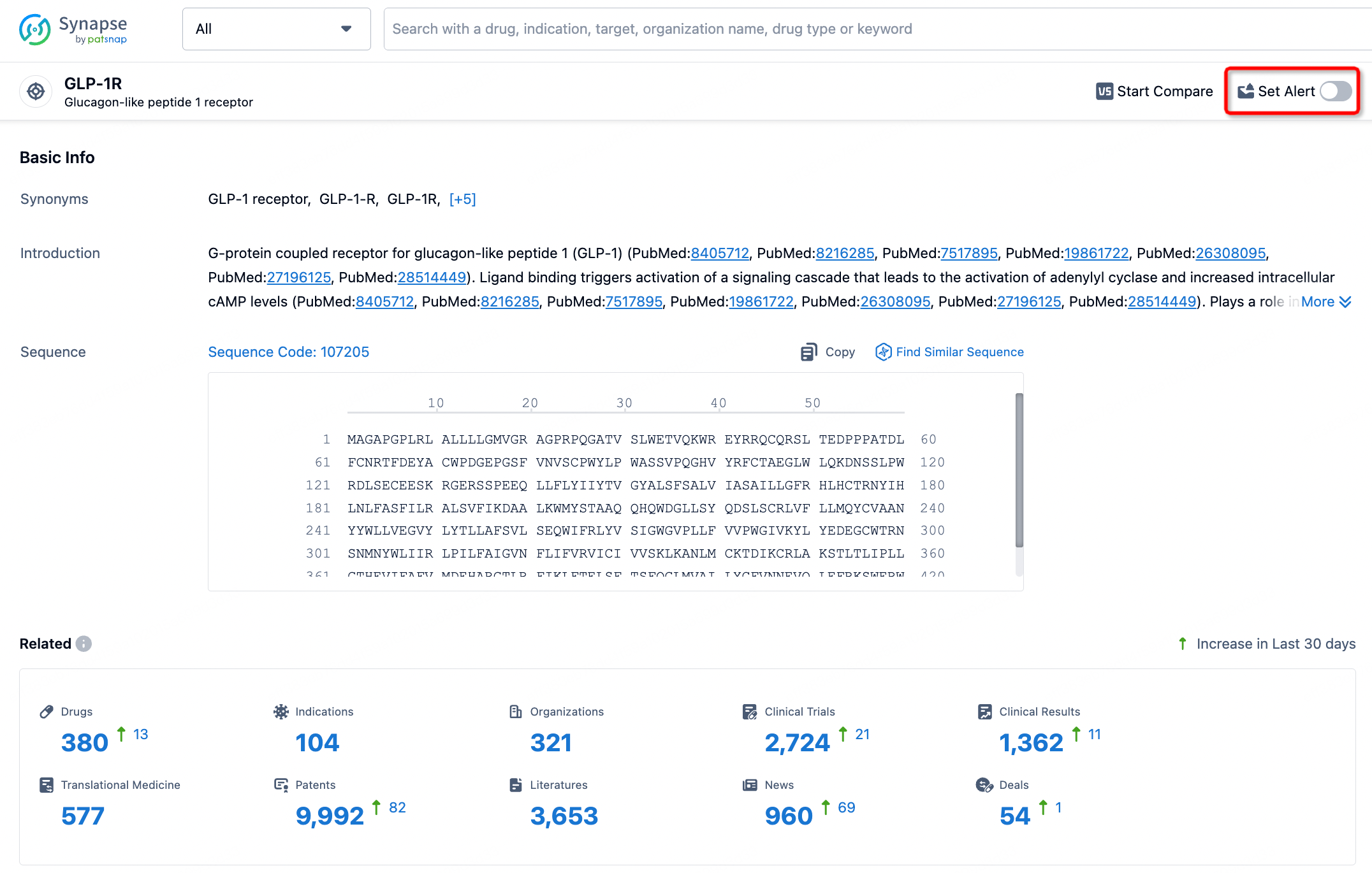
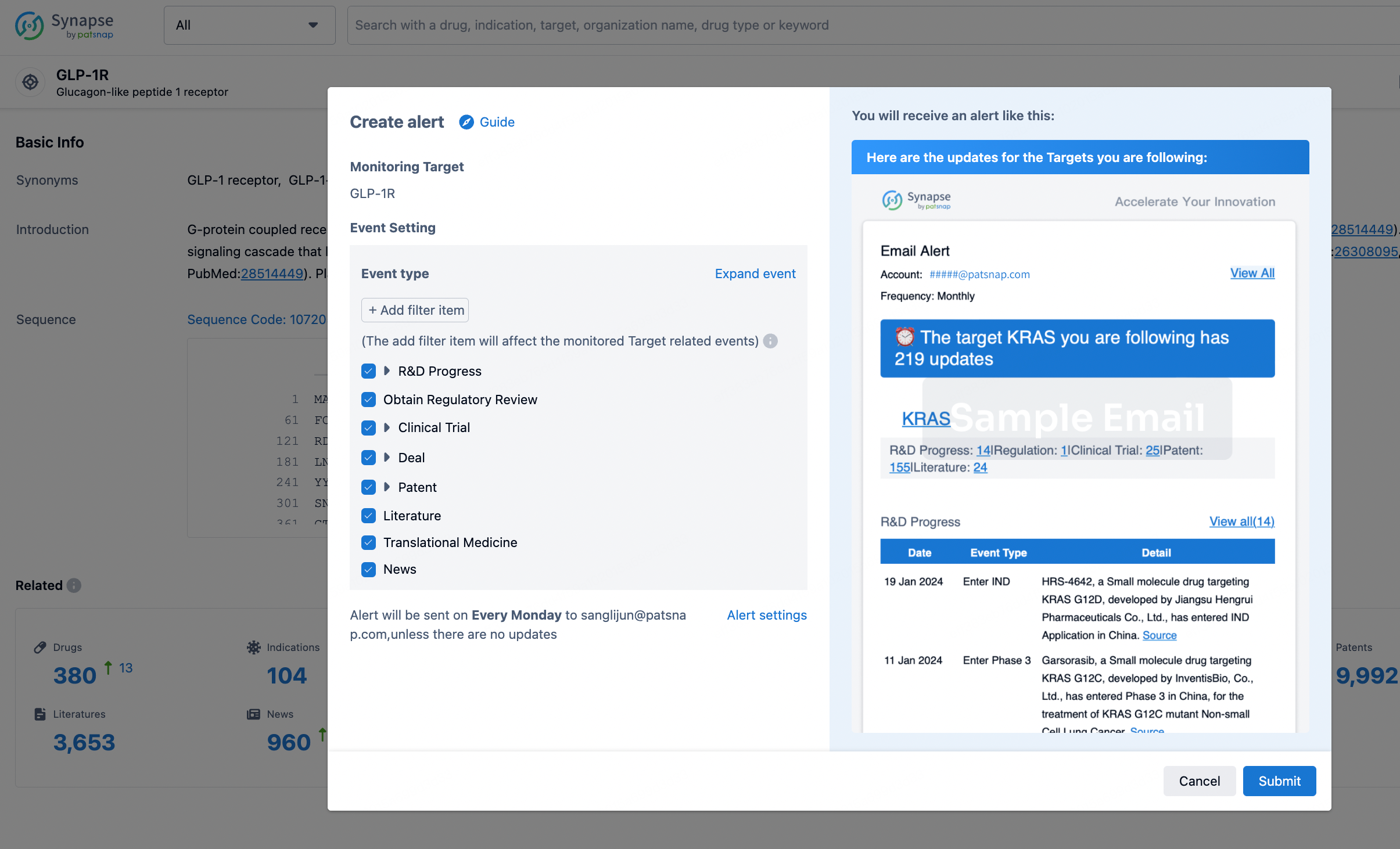
How to obtain the latest development progress of all targets?
In the Synapse database, you can stay updated on the latest research and development advances of all targets. This service is accessible anytime and anywhere, with updates available daily or weekly. Use the "Set Alert" function to stay informed. Click on the image below to embark on a brand new journey of drug discovery!
AI Agents Built for Biopharma Breakthroughs
Accelerate discovery. Empower decisions. Transform outcomes.
Get started for free today!
Accelerate Strategic R&D decision making with Synapse, PatSnap’s AI-powered Connected Innovation Intelligence Platform Built for Life Sciences Professionals.
Start your data trial now!
Synapse data is also accessible to external entities via APIs or data packages. Empower better decisions with the latest in pharmaceutical intelligence.