Request Demo
What are IDS stimulators and how do they work?
21 June 2024
Intrusion Detection Systems (IDS) stimulators have become an integral part of modern cybersecurity strategies, playing a pivotal role in ensuring the robustness and efficacy of IDS implementations. These stimulators are specialized tools designed to test and validate the capabilities of IDS by simulating various attack scenarios, ensuring that the IDS can detect and respond to potential threats effectively. To understand the significance of IDS stimulators, it is essential to delve into how they operate and their practical applications in the cybersecurity landscape.
At their core, IDS stimulators work by creating controlled, realistic simulations of cyber-attacks and malicious activities within a network environment. These simulations are meticulously crafted to mimic the tactics, techniques, and procedures (TTPs) employed by real-world attackers. By generating benign and malicious traffic, IDS stimulators allow cybersecurity professionals to assess how well a given IDS can detect and differentiate between normal and anomalous activities.
The operation of an IDS stimulator typically involves several stages. Initially, the stimulator generates a variety of network traffic that includes both legitimate and malicious activities. This traffic is then injected into the network where the IDS is deployed. The IDS continuously monitors this traffic to identify patterns and anomalies that indicate potential security threats.
Once the traffic is analyzed, the IDS generates alerts based on predefined rules and algorithms. These alerts are then evaluated to determine the accuracy and effectiveness of the IDS in identifying the simulated attacks. The results provide valuable insights into the IDS’s performance, highlighting strengths and identifying areas that require improvement. This iterative process of testing and refining ensures that the IDS remains capable of defending against evolving cyber threats.
IDS stimulators are employed for a myriad of purposes, each contributing to the overarching goal of fortifying an organization’s cybersecurity posture. One of the primary uses of IDS stimulators is in the validation and tuning of IDS configurations. By simulating various attack vectors, stimulators help security teams fine-tune the IDS settings to minimize false positives and false negatives. This fine-tuning is crucial for maintaining an optimal balance between security and usability, ensuring that legitimate activities are not inadvertently flagged as threats.
Another key application of IDS stimulators is in the context of security training and awareness. Cybersecurity teams can use stimulators to create training scenarios that replicate real-world attack scenarios. This hands-on training helps security personnel develop their skills in detecting and responding to threats, enhancing their preparedness for actual incidents. Additionally, these simulations can be used to educate employees across the organization about the importance of cybersecurity and the role of IDS in safeguarding sensitive data.
Moreover, IDS stimulators play a critical role in the evaluation and benchmarking of different IDS solutions. Organizations can leverage stimulators to conduct comparative analyses of various IDS products, assessing their performance under identical conditions. This objective evaluation aids in selecting the most suitable IDS solution that aligns with the organization’s specific security requirements and infrastructure.
In the realm of compliance and auditing, IDS stimulators offer significant value. Regulatory standards and frameworks often mandate rigorous testing of security controls to ensure compliance. By employing IDS stimulators, organizations can demonstrate their commitment to maintaining robust security measures, thereby meeting regulatory requirements and avoiding potential penalties.
Furthermore, IDS stimulators contribute to proactive threat hunting efforts. By simulating emerging threat scenarios, security teams can proactively identify vulnerabilities and weaknesses within their network defenses. This proactive approach enables organizations to implement necessary countermeasures before adversaries can exploit these vulnerabilities, thereby reducing the risk of successful attacks.
In conclusion, IDS stimulators are indispensable tools in the cybersecurity arsenal, enabling organizations to validate, optimize, and enhance the effectiveness of their Intrusion Detection Systems. Through realistic attack simulations, they provide valuable insights into IDS performance, support security training initiatives, aid in product evaluation, ensure regulatory compliance, and facilitate proactive threat hunting. As the cyber threat landscape continues to evolve, the role of IDS stimulators in fortifying network defenses will only become more critical, underscoring their importance in safeguarding digital assets and maintaining cyber resilience.
At their core, IDS stimulators work by creating controlled, realistic simulations of cyber-attacks and malicious activities within a network environment. These simulations are meticulously crafted to mimic the tactics, techniques, and procedures (TTPs) employed by real-world attackers. By generating benign and malicious traffic, IDS stimulators allow cybersecurity professionals to assess how well a given IDS can detect and differentiate between normal and anomalous activities.
The operation of an IDS stimulator typically involves several stages. Initially, the stimulator generates a variety of network traffic that includes both legitimate and malicious activities. This traffic is then injected into the network where the IDS is deployed. The IDS continuously monitors this traffic to identify patterns and anomalies that indicate potential security threats.
Once the traffic is analyzed, the IDS generates alerts based on predefined rules and algorithms. These alerts are then evaluated to determine the accuracy and effectiveness of the IDS in identifying the simulated attacks. The results provide valuable insights into the IDS’s performance, highlighting strengths and identifying areas that require improvement. This iterative process of testing and refining ensures that the IDS remains capable of defending against evolving cyber threats.
IDS stimulators are employed for a myriad of purposes, each contributing to the overarching goal of fortifying an organization’s cybersecurity posture. One of the primary uses of IDS stimulators is in the validation and tuning of IDS configurations. By simulating various attack vectors, stimulators help security teams fine-tune the IDS settings to minimize false positives and false negatives. This fine-tuning is crucial for maintaining an optimal balance between security and usability, ensuring that legitimate activities are not inadvertently flagged as threats.
Another key application of IDS stimulators is in the context of security training and awareness. Cybersecurity teams can use stimulators to create training scenarios that replicate real-world attack scenarios. This hands-on training helps security personnel develop their skills in detecting and responding to threats, enhancing their preparedness for actual incidents. Additionally, these simulations can be used to educate employees across the organization about the importance of cybersecurity and the role of IDS in safeguarding sensitive data.
Moreover, IDS stimulators play a critical role in the evaluation and benchmarking of different IDS solutions. Organizations can leverage stimulators to conduct comparative analyses of various IDS products, assessing their performance under identical conditions. This objective evaluation aids in selecting the most suitable IDS solution that aligns with the organization’s specific security requirements and infrastructure.
In the realm of compliance and auditing, IDS stimulators offer significant value. Regulatory standards and frameworks often mandate rigorous testing of security controls to ensure compliance. By employing IDS stimulators, organizations can demonstrate their commitment to maintaining robust security measures, thereby meeting regulatory requirements and avoiding potential penalties.
Furthermore, IDS stimulators contribute to proactive threat hunting efforts. By simulating emerging threat scenarios, security teams can proactively identify vulnerabilities and weaknesses within their network defenses. This proactive approach enables organizations to implement necessary countermeasures before adversaries can exploit these vulnerabilities, thereby reducing the risk of successful attacks.
In conclusion, IDS stimulators are indispensable tools in the cybersecurity arsenal, enabling organizations to validate, optimize, and enhance the effectiveness of their Intrusion Detection Systems. Through realistic attack simulations, they provide valuable insights into IDS performance, support security training initiatives, aid in product evaluation, ensure regulatory compliance, and facilitate proactive threat hunting. As the cyber threat landscape continues to evolve, the role of IDS stimulators in fortifying network defenses will only become more critical, underscoring their importance in safeguarding digital assets and maintaining cyber resilience.
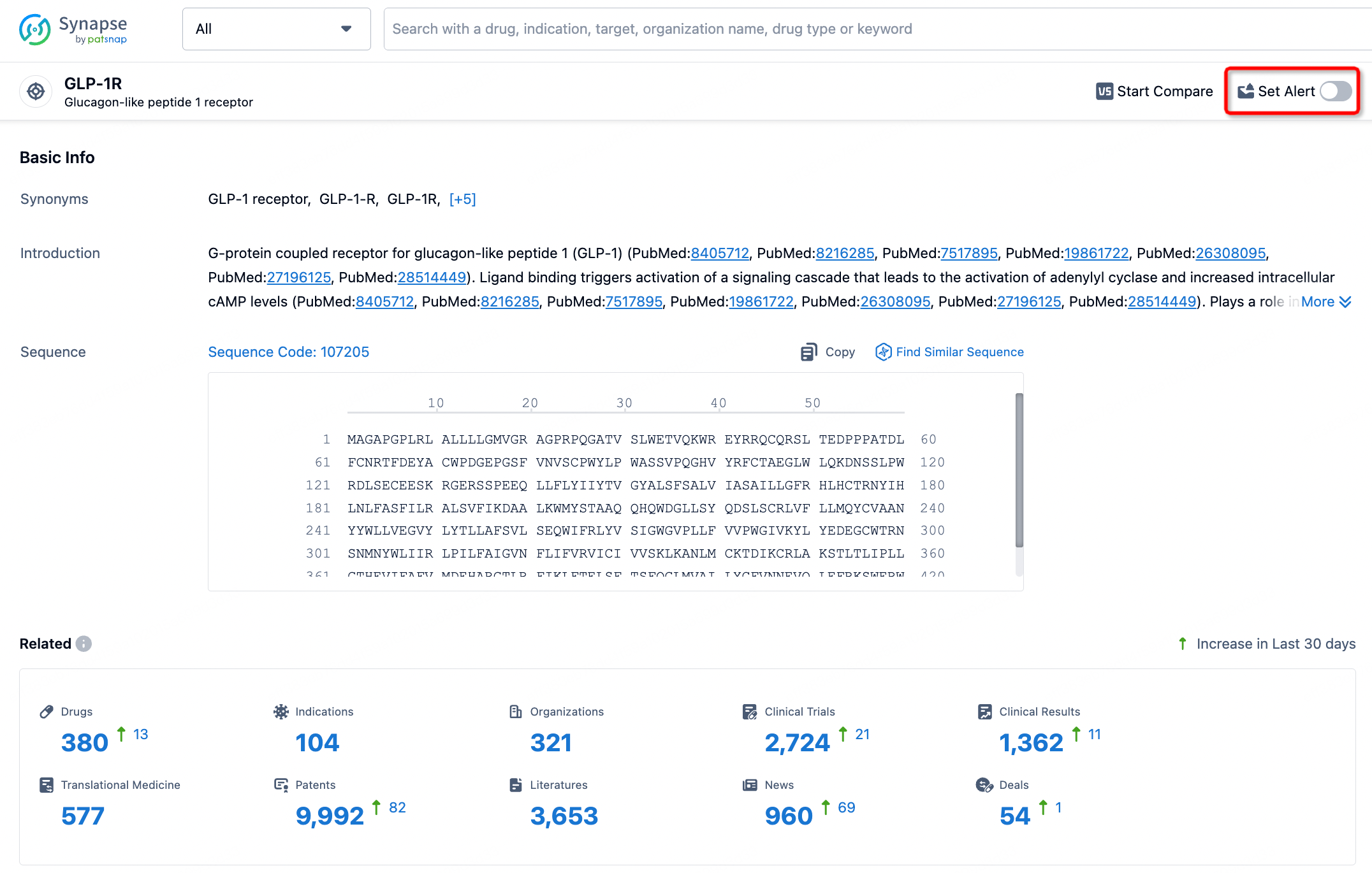
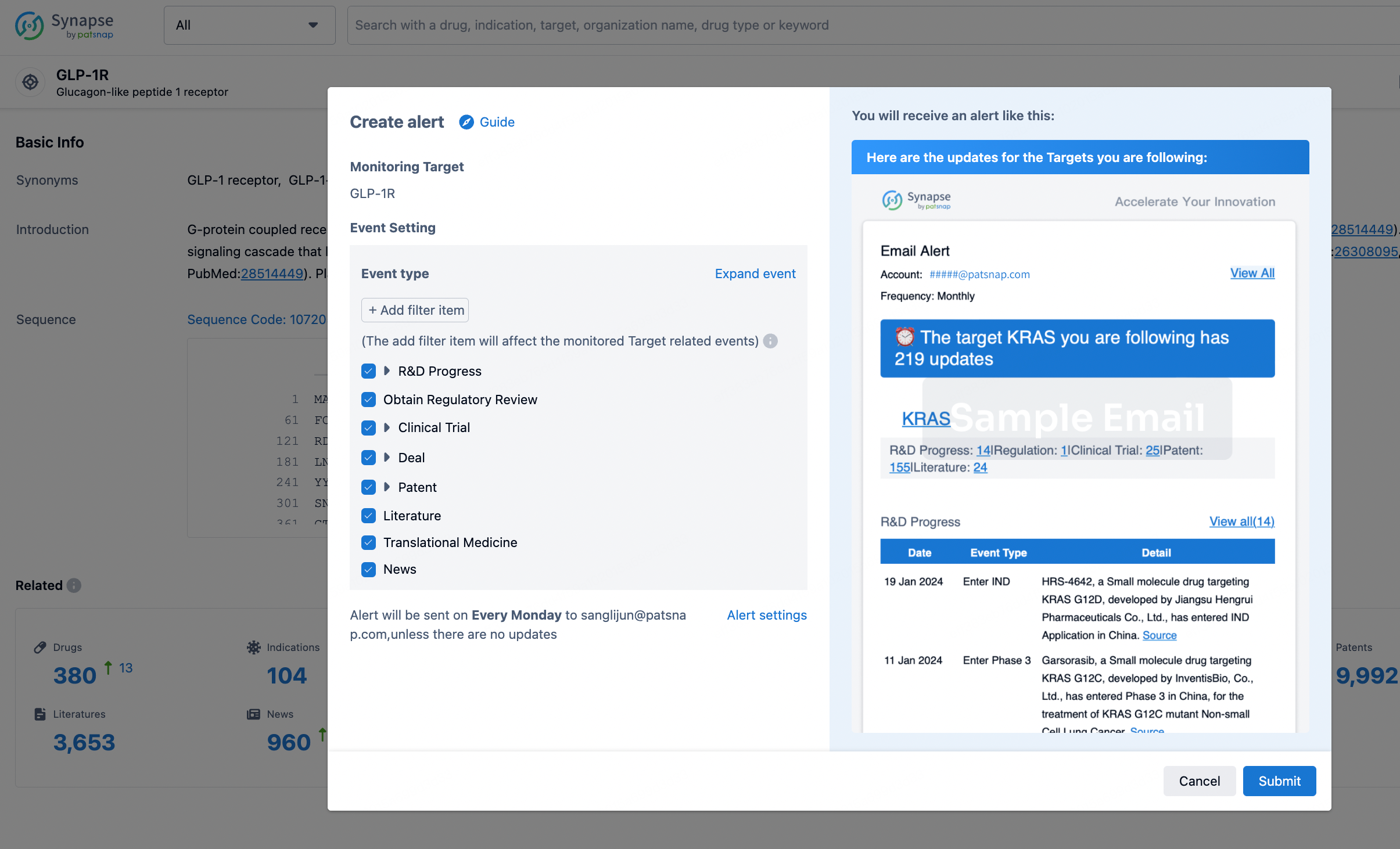
How to obtain the latest development progress of all targets?
In the Synapse database, you can stay updated on the latest research and development advances of all targets. This service is accessible anytime and anywhere, with updates available daily or weekly. Use the "Set Alert" function to stay informed. Click on the image below to embark on a brand new journey of drug discovery!
AI Agents Built for Biopharma Breakthroughs
Accelerate discovery. Empower decisions. Transform outcomes.
Get started for free today!
Accelerate Strategic R&D decision making with Synapse, PatSnap’s AI-powered Connected Innovation Intelligence Platform Built for Life Sciences Professionals.
Start your data trial now!
Synapse data is also accessible to external entities via APIs or data packages. Empower better decisions with the latest in pharmaceutical intelligence.